Nivdort
Original Issue Date:-
June 06, 2016
Virus Type:-
Trojan
Severity:-
High
It has been reported that the variants of new data stealing Trojan named as
The malware is capable of performing the following function:
- Steals sensitive information from the victim's machine including stored username and passwords, cache data, cookies, etc.
- Capable of capturing keystrokes and screen capture.
- Collects data about installed applications
- Modifies windows Host File of the infected machine.
- Make network connections to send exfiltrated data to remote server.
- Use code injection technique to evade detection.
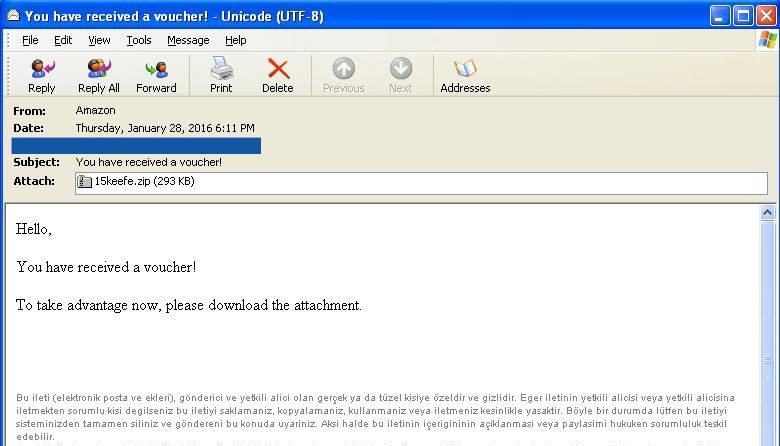
Sample spam email is shown below:
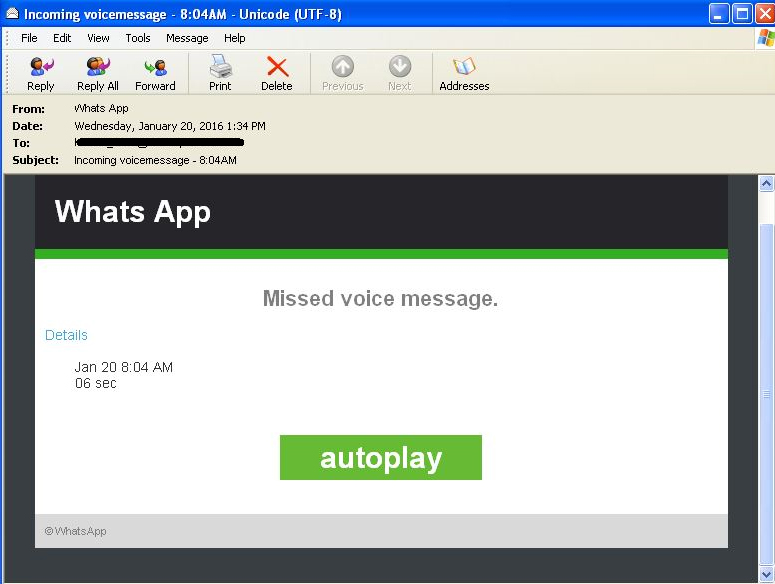
Delivering malware as a fake WhatsApp content in emails as shown below.
Aliases:Trojan.Win32.Scar.jifn [Kaspersky], Troj/Nivdor-A [Sophos], Downloader.Upatre!g15 [Symantec], TrojanSpy: Win32/Nivdort.BE [Microsoft], Win32/Nivdort.Z [Microsoft],Trojan.KillFiles.19733 [Dr.Web], W32/Kryptik.CCLE!tr[Fortinet],TROJ_WONTON.SMJ1 [other], Trojan-FEMT!FCFC168625FE [McAfee]
Installations: For initial installation malware make some file system changes and later injects its code into the legitimate processes running on the victim's machine.
File system changes: Malware drops a copy of itself with random name in system folders including < system folder > , %temp%, %Appdata%, %system root%/temp etc in the following pattern:
- < system folder > / < random folder name > < random file name > .exe
- %temp%/ < random folder name > < random file name > .exe
- %Appdata%/ < random folder name > < random file name > .exe
- %system root%/temp/ < random folder name > < random file name > .exe
Some of the file system changes are:
- %APPDATA%\cgqveqeppxy\ekrpepkr.exe
- %APPDATA%\cgqveqeppxy\sjhejkqavhna.exe
- %SystemRoot% \temp\bklp39qp1syfg.exe
- < system folder > \bispxdqwmc.exe
- %TEMP% \pouyn354hxzyfgxcnulx.exe
- c:\egbiarlfwps\lx1ym3phmkfjprdqk.exe
- c:\egbiarlfwps\pfmkybnb.exe
- c:\egbiarlfwps\uceyyfn.exe
Other file system changes include creation of configuration files in with the name as Cfg,etc, rng, run or tst.
Registry changes:
Registry changes made by the malware for persistence are:
- In subkey:HKCU \ software \ microsoft \ windows\ currentversion\run
Sets value:"VC Scheduler Registry Interface Secure Connect"
With data:"%APPDATA%\cgqveqeppxy\sjhejkqavhna.exe" - In subkey: HKLM\Software\Microsoft\Windows\CurrentVersion\Run
With data: "Endpoint Controls WinHTTP Web"
Sets value: " < system folder > \bispxdqwmc.exe"
Disable Firewall:
Adds value: "FirewallDisableNotify"
With data: "1"
To subkey: HKLM\SOFTWARE\Microsoft\Security Center
Network Connections: To establish network connections, malware first checks victims machine network settings, if network connection found, it establishes communication with the remote server to receive commands from attacker and upload stolen data accordingly. Malware may also receive other malicious binaries from remote server for execution on the victim machine. It is shown below:
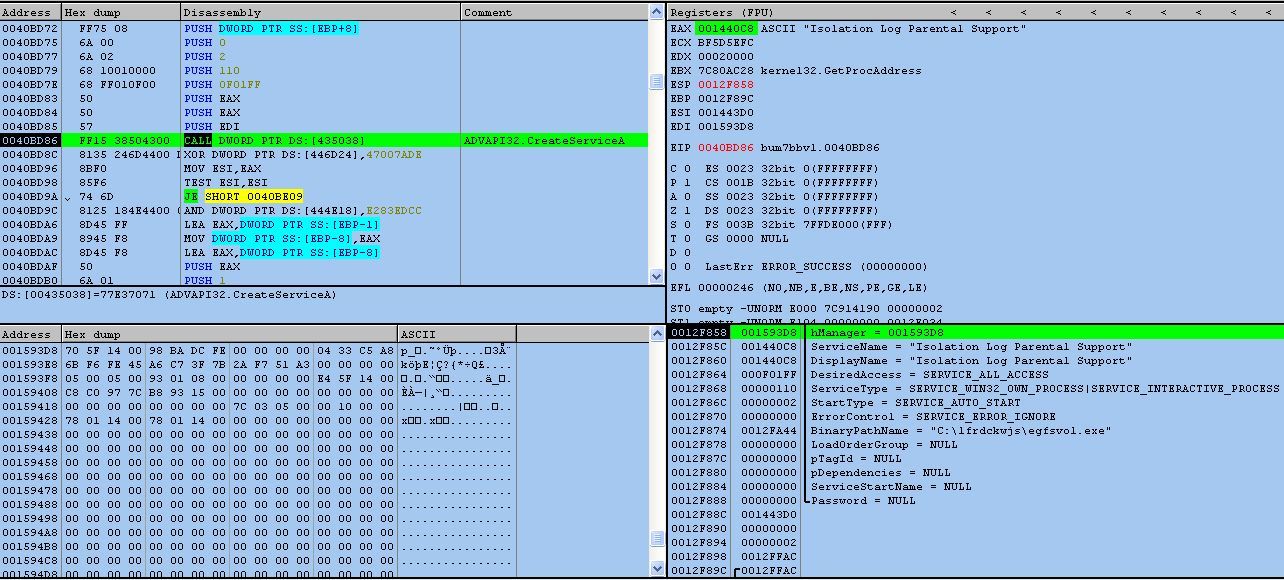
Some of the C2 servers used by the malware for communication on port 80 are:
- thoughtsuccess[dot]net
- thoughtbanker[dot]net
- summersuccess[dot]net
- thoughtspring[dot]net
- watersuccess[dot]net
- summerbanker[dot]net
- summerspring[dot]net
- crowdsuccess[dot]net
- thoughtfound[dot]net
- crowdspring[dot]net
- weathercontinue[dot]net
- strangecontinue[dot]net
- morningdiscover[dot]net
- morningcontinue[dot]net
- weatherdiscover[dot]net
- historydiscover[dot]net
- strangediscover[dot]net
- historycontinue[dot]net
- presentindustry[dot]net
- collegeindustry[dot]net
- groupguess[dot]net
- jarybuter[dot]com
- mojoguia[dot]com
- mojositio[dot]com
- spokefirst[dot]net
- spokeguess[dot]net
- spokekill[dot]net
[Replace "[dot]" with "." For actual URL.]
There are several other C2 servers used by the malware for remote communications. The domain details are mentionedin virus alerts issued by different vendors, URLs of different virus details from different AV vendors are given in reference section.
Countermeasures:
- Delete the system changes made by the malware such as files created/ registry entries /services etc.
- Monitor traffic generated from client machines to the domains and IP address mentioned in Installation section.
- Exercise caution while opening email received pretending to be from WhatsApp.
- Set Internet and Local intranet security zone settings to "High" to block ActiveX Controls and Active Scripting in these zones
- Scan infected system with updated versions of Antivirus solution
- Enable Autorun and Autoplay policies on end user system.
- Use limited privilege user on the computer or allow administrative access to systems with special administrative accounts for administrators
- Limiting or eliminating the use of shared or group accounts
- Do not visit websites/URLs received from untrusted sources or unexpectedly received from known sources.
- Do not download or open attachment in emails received from untrusted sources or unexpectedly received from trusted users.
- Enforce a strong password policy and implement regular password changes.
- Enable a personal firewall on workstation.
- Install and scan anti malware engines and keep them up-to-date.
- Isolate compromised computers quickly to prevent threats from spreading further. Perform a forensic analysis and restore the computers using trusted media.
- Configure email server to block or remove email containing file attachments that are commonly used to spread threats, such as .vbs, .bat, .exe, .pif and .scr files.
- Disable unnecessary services on user workstations and servers, if not in use.
- Maintain situational awareness of the latest threats; implement appropriate ACLs.
References:
- https://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=TrojanSpy%3AWin32%2FNivdort.Z&ThreatID=-2147275962
- https://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=TrojanSpy:Win32/Nivdort.BE
- https://www.sophos.com/en-us/threat-center/threat-analyses/viruses-and-spyware/Troj~Nivdor-A.aspx
- https://www.sophos.com/en-us/threat-center/threat-analyses/viruses-and-spyware/Troj~Nivdor-A/detailed-analysis.aspx
- https://www.microsoft.com/security/portal/threat/Encyclopedia/Entry.aspx?Name=Win32/Nivdort
- https://www.sophos.com/en-us/threat-center/threat-analyses/viruses-and-spyware/Troj~Nivdort-BV/detailed-analysis.aspx
- https://blogs.mcafee.com/mcafee-labs/nivdort-data-stealing-trojan-arrives-via-spam/


