Sodin Ransomware
Original Issue Date:-
July 11, 2019
Virus Type:- Ransomware
Severity:-
High
It has been observed that the variants of ransomware named as Sodin aka Sodinokibi and REvil exploiting a recently discovered Windows zero day Vulnerability are spreading. The malware first observed in early 2019, exploiting Oracle Weblogic vulnerability and attacking MSP providers. Later, it has been discovered that the malware is capable of exploiting Microsoft Windows zero day vulnerability which is "CVE-2018-8453" for privilege escalation. The malware is capable of performing the following functions:
- Exploits Oracle Weblogic vulnerability and Microsoft Windows zero day vulnerability which is "CVE-2018-8453"
- Make network connections to remote Command and control server hardcoded in malware configuration file in encrypted format.
- Uses hybrid scheme of encryption which is “Salsa20 symmetric stream” algorithm for encrypting files and “elliptic curve asymmetric” algorithm for keys.
- Uses arbitrary extensions for encrypted files.
- Sends exfiltrated data to remote command and control server in an encrypted format using ECIES algorithm (Elliptical curve cryptography).
- Checks for the Victim’s machine CPU configurations and run shellcode accordingly.
The malware exploits a vulnerability in Win32k.sys windows component to gain elevated privileges. Upon successful exploitation, the attacker gains highest privileges to deploy its malicious shellcode and execute commands. The malware code has an encrypted configuration block that contains all the settings and data required for the functioning of the malware. The decrypted configuration settings are shown as below:
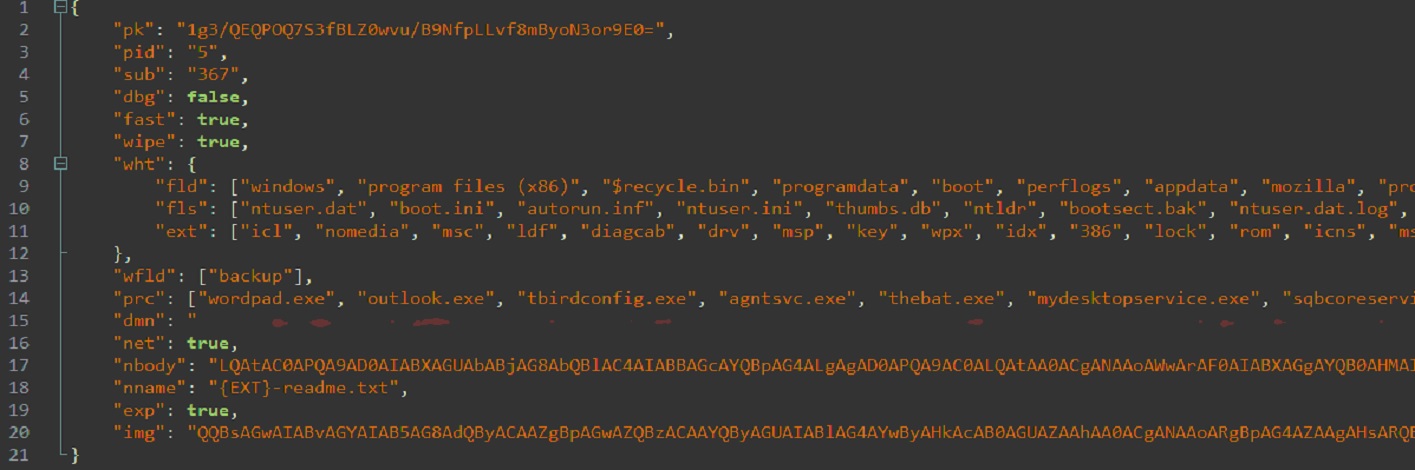
The configuration block contains information such as public key, campaign ID, remote server configurations, ransom note, exploit, name of processes to be terminated, name of directories targeted for file creation and deletion, list of file types not to be encrypted etc.
Network Communication
The malware is capable of making network connections and send victim machine information to remote command and control server based on a flag set in its configuration block. The information sent to remote server includes machine name, Operating system information, machine workgroup/domain, infection ID, username, trojan version, campaign ID, OS architecture, system drives information, encrypted files extension, keyboard layout and system language, etc.
Indicator of Compromise:
Malware Hash: 1ce1ca85bff4517a1ef7e8f9a7c22b16
Countermeasures:
- Users are advised to disable their RDP if not in use, if required it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Restrict execution of Power shell /WSCRIPT in enterprise environment Ensure installation and use of the latest version (currently v5.0) of PowerShell, with enhanced logging enabled. Script block logging, and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
Reference: https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html - Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf.
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Patch the Microsoft Windows vulnerability CVE-2018-8453 exploited in the attack.
Reference: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8453
References:
- https://securelist.com/sodin-ransomware/91473/
- https://www.kaspersky.com/blog/sodin-msp-ransomware/27530/
- https://www.darkreading.com/perimeter/sodin-ransomware-exploits-windows-privilege-escalation-bug/d/d-id/1335145
- https://threatpost.com/new-sodinokibi-ransomware-exploits-critical-oracle-weblogic-flaw/144233/
- https://exchange.xforce.ibmcloud.com/collection/0354ae335c04904f429ee242b234ee01
- https://securityaffairs.co/wordpress/87944/malware/sodin-ransomware-cve-2018-8453.html
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8453
- https://www.cyberark.com/threat-research-blog/sodin-ransomware/
- https://www.computerweekly.com/news/252466220/Sodin-ransomware-exploiting-Windows-zero-day-Kaspersky-warns
- https://securityboulevard.com/2019/07/sodin-ransomware/


