Trojan Glupteba
Original Issue Date:-
May 05, 2018
Virus Type:-
Trojan
Severity:-
High
Several variants of Trojan Glupteba with updated functionalities are reported. This Trojan arrives on a system as a file dropped by other malware or by exploit kits when users are being unknowingly routed to malicious sites. Generally the malware installs itself as a service and enable persistent mechanisms on the victim machine posing as updation legit software. The malware communicates to hardcoded IP addresses and ports.
The IP list may contain legit / compromised resources as well.
Sample communication:
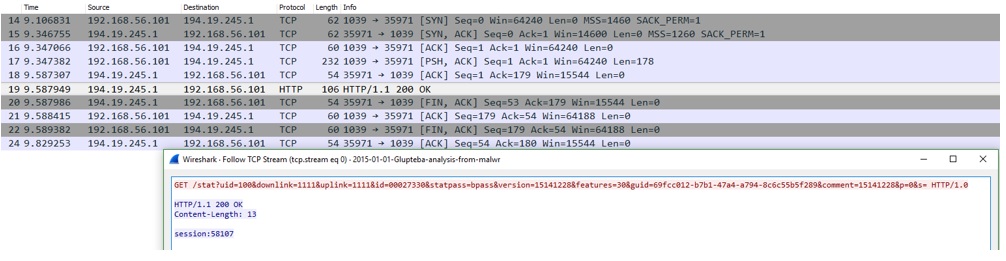
Fig 1. Representation of sample communication
Generated traffic towards:
Domains
- ostdownload.xyz
- travelsreview.wo rld
- bigdesign.website
- sportpics.xyz
- kinosport.top
- 0ev.ru
- 0df.ru
- 0d2.ru
- 0d9.ru
IP address
- 109[.]104.94.2:11754
- 172[.]245.29.128:45297
- 174[.]34.232.88:49649
- 184[.]154.128.82:31973
- 192[.]184.35.170:52112
- 212[.]48.66.150:22357
- 41[.]77.118.74:57136
- 50[.]116.54.156:46956
- 65[.]60.11.122:49021
- 70[.]32.107.132:19796
- 72[.]13.32.43:29755
- 82[.]98.104.7:30871
- 87[.]98.188.159:15206
- 5[.]101.6.132
- 5[.]79.87.139
- 5[.]79.87.153
- 5[.]8.10.194
- 37[.]48.81.151
- 46[.]165.244.129
- 46[.]165.249.167
- 46[.]165.249.195
- 46[.]165.249.201
- 46[.]165.249.203
- 46[.]165.250.25
- 78[.]31.67.205
- 78[.]31.67.206
- 80[.]93.90.27
- 80[.]93.90.32
- 80[.]93.90.69
- 80[.]93.90.72
- 80[.]93.90.78
- 80[.]93.90.84
- 81[.]30.152.25
- 85[.]114.135.113
- 85[.]114.141.81
- 89[.]163.206.137
- 89[.]163.206.174
- 89[.]163.212.9
- 91[.]121.65.98
- 91[.]216.93.126
- 91[.]216.93.20
- 109[.]238.10.78
- 178[.]162.193.193
- 178[.]162.193.195
- 178[.]162.193.66
- 178[.]162.193.86
- 193[.]111.140.238
- 193[.]111.141.213
- 212[.]92.100.114
- 212[.]92.100.115
- 213[.]202.254.161
- 213[.]5.70.9
- 217[.]79.189.227
File system
- 623F4A6CD5947CA0016D3E33A07EB72E8C176BA cloudnet.exe
- ED310E5B9F582B4C6389F7AB9EED17D89497F277 cloudnet.exe
- F7230B2CAB4E4910BCA473B39EE8FD4DF394CE0D setup.exe
- 70F2763772FD1A1A54ED9EA88A2BCFDB184BCB91 cloudnet.e xe
- 87AD7E248DADC2FBE00D8441E58E64591D9E3CBE cloudnet.exe
- 1645AD8468A2FB54763C0EBEB766DFD8C643F3DB csrss.exe
- 09708c49ffb1556c9b80b3a2dc1f57fe
- %UserProfile%\Local Settings\Applica tion Data\NVIDIA Corporation\Updates\NvdUpd.exe
- %UserProfile%\Local Settings\Application Data\NVIDIA Corporation\Updates\NvdUpd.exe .bak
- HKEY_CURRENT_USER\Software\NVIDIA Corporation\Global\nvUpdSrv\"value" = "[GENERIC N UMBER]"
- HKEY_CURRENT_USER\Software\NVIDIA Corporation\Global\nvUpdSrv\"GUID" = "[GENERIC GUID]"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\"NvUpdSrv" =
- "%UserProfile%\Local Settings\Application Data\NVIDIA Corporation\Updates\NvdUpd.exe
- Global\MD7H82HHF7EH2D73 [Mutex]
Recommendations:
- CERT-IN recommends monitoring activity to the IP(s) / Domains as a potential indicator of infection.
- Disable macros in Microsoft Office products. Some Office products allow for the disabling of macros that originate from outside of an organization and can provide a hybrid approach when the organization depends on the legitimate use of macros. For Windows, specific settings can block macros originating from the Internet from running.
- Restrict execution of powershell /WSCRIPT in enterprise environment Ensure installation and use of the
latest version (currently v5.0) of PowerShell, with enhanced logging enabled. script block logging, and
transcription enabled. Send the associated logs to a centralized log repository for monitoring and
analysis.
Reference: https://www.fireeye.com/blog/threatresearch/2016/02/greater_visibilityt.html. - Deploy web and email filters on the network. Configure these devices to scan for known bad domains, sources, and addresses; block these before receiving and downloading messages. Scan all emails,attachments, and downloads both on the host and at the mail gateway with a reputable antivirus solution. Note: A lot of malicious domains are using TLDs of (.PW, .TOP, .ME) and DYNDNS domains. Monitor connections to such domains Enforce application whitelisting on all endpoint workstations. This will prevent droppers or unauthorized software from gaining execution on endpoints..
References:


