Double Locker Android Ransomware
Original Issue Date:-
October 27, 2017
Type:-
Ransomware
Severity:-
Medium
It has been reported that a new ransomware called DoubleLocker targeting Android devices. The malware spreads through counterfeit applications (mostly fake Adobe Flash Player) via compromised websites. It abuses Android accessibility services to elevate privileges on the victim system. The malware changes the devices PIN and encrypts all the files on the device’s primary storage using AES encryption algorithm and renames the file to have the extension ‘.cryeye’ and demands ransom to decrypt them.
Malware Activities
When it is launched the app requests for the accessibility service permissions. Once it gains access to the permissions, it sets itself as the default Home screen application so that it can be activated whenever the user presses the Home key on their Android phone.
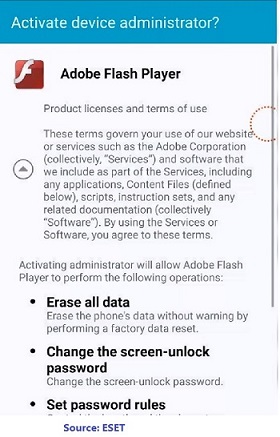
The malware once activated, changes the device’s PIN to a random value, thus locking the user out of their phone. The PIN is neither stored on the device nor sent to any server. It can only be reset remotely by the attacker once the ransom is paid.
The malware encrypts all the files on the device’s primary storage using AES encryption algorithm and renames the file to have the extension ‘.cryeye’. The user is then shown a screen in which the attacker demands a ransom for decrypting the user’s file. The ransom is 0.013 Bitcoins and it must be paid within 24 hours. If the ransom is not paid, the data would remain encrypted and would not be deleted.

Recovery of the encrypted files are not possible as of now, the safest way to remove the malware is to factory-reset. However, the PIN lock can be bypassed on “ROOT”ed android devices with Android Debugging mode enabled, via Android Debug Bridge and removing the related key files [generally /data/system/password.key].
Best Practices
- Do not download and install applications from untrusted sources. Install applications downloaded from reputed application market only.
- Make a practice of taking regular backup of android device.
- Prior to downloading / installing apps on android devices (even from Google Play Store):
- Alwars review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- Do not check "Untrusted Sources" checkbox to install side loaded apps.
- Exercise caution while visiting trusted/untrusted sites for clicking links.
- Install and maintain updated antivirus solution on android devices.Scan the suspected device with antivirus solutions to detect and clean infections.
- Refer to security best practices for mobile Phone users:
http://www.cyberswachhtakendra.gov.in/documents/Mobile_phone_Security.pdf - Install Android updates and patches as and when available from Android device vendors
- Enable 2-factor authentication for your Google/other accounts.
- Users are advised to use device encryption or encrypting external SD card feature available with most of the android OS
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
References
- https://www.welivesecurity.com/2017/10/13/doublelocker-innovative-android-malware/
- http://www.csoonline.in/news/double-locker-two-step-ransomware-exposed


