Doki
Original Issue Date:- August 03, 2020
Virus Type:- Backdoor
Severity:- Medium
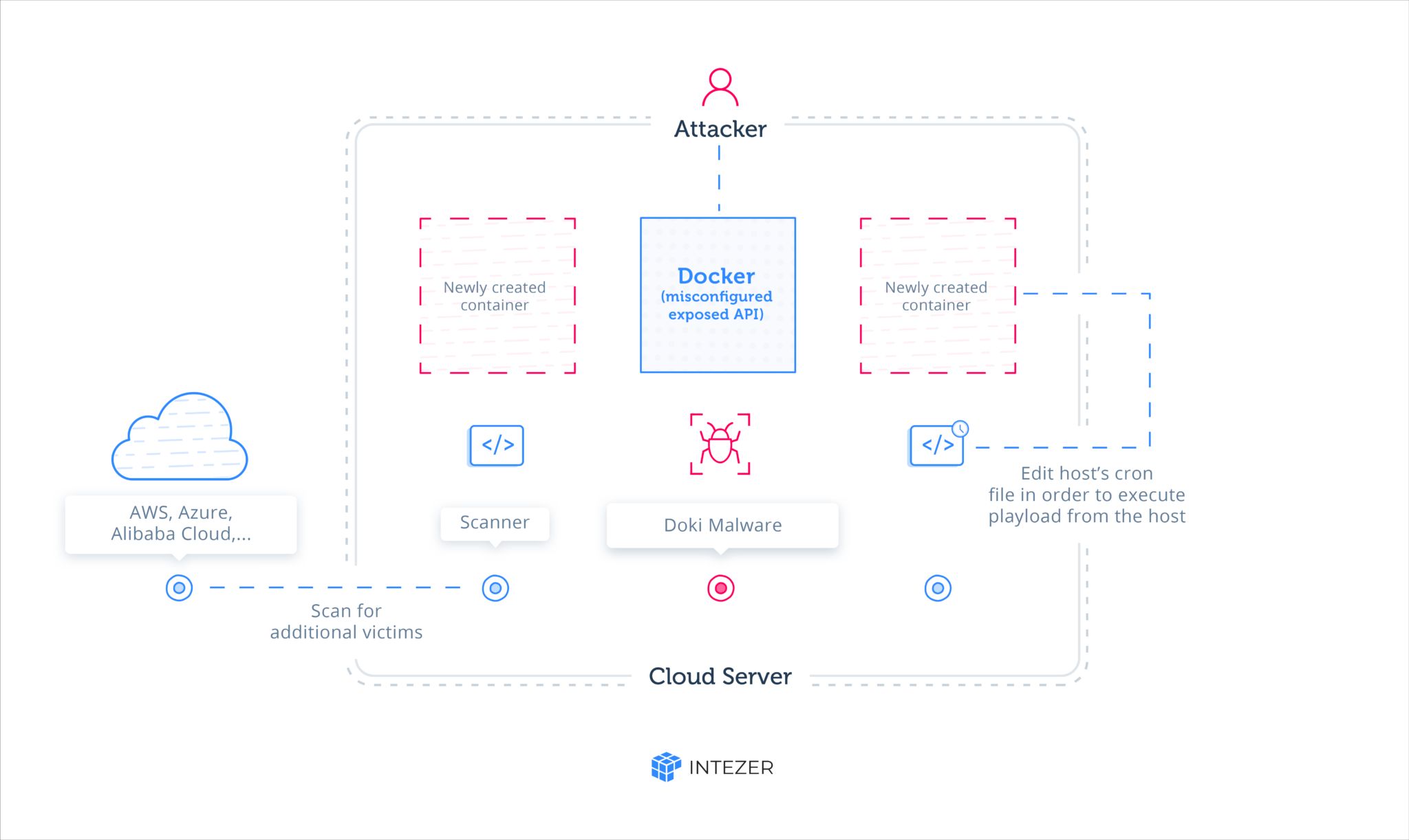
It has been observed that a new sophisticated Linux OS based backdoor named ‘Doki’ is spreading. The attackers are exploiting the booming cloud computing infrastructure which is usually based on Linux architecture to attack Linux systems and servers. The attackers target publically accessible Docker servers hosted with popular cloud platforms, including, AWS, Azure and Alibaba Cloud. Docker is a famous platform-as-a-service (PaaS) solution for developers to create, test and run their applications in a loosely isolated environment called container. This attack is very dangerous due to the fact the attacker uses container escape techniques to gain full control of the victim’s infrastructure.
Infection Mechanism
The attackers are abusing misconfigured Docker API ports, where attackers scan for publicly accessible Docker servers and exploit them in order to set up their own containers and execute malware on the victim’s infrastructure. Doki uses a complex mechanism to contact its operator by abusing the Dogecoin cryptocurrency blockchain to generate dynamic addresses.
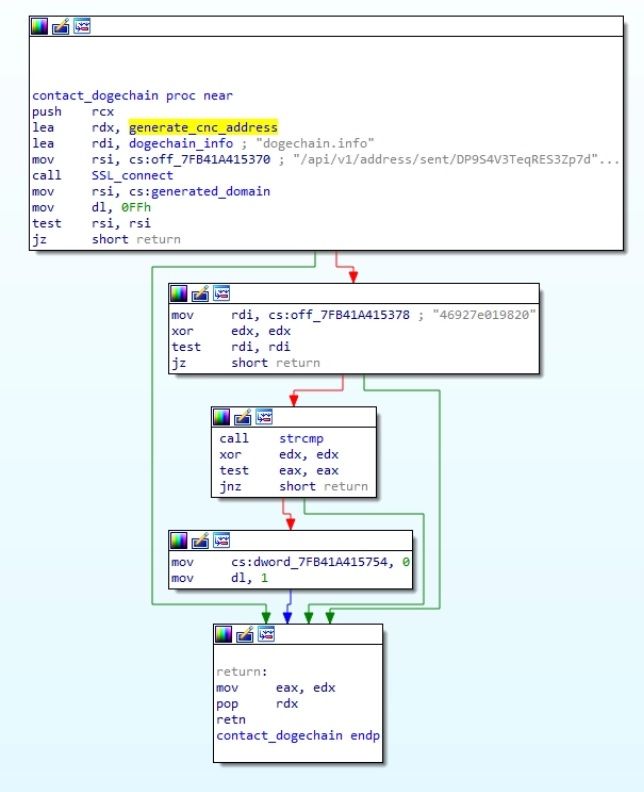
DOKI utilizes the DynDNS service and a unique Domain Generation Algorithm (DGA) based on the Dogecoin cryptocurrency blockchain in order to find the domain of its C2 in real time.
To generate C2 address, DOKI firstly queries dogechain.info API for getting the value sent out from hardcoded wallet address controlled by attacker. SHA256 is performed on the value returned. The first 12 digits of SHA256 appended with”ddns.net” becomes the full address such as 6d77335c4f23.ddns.net. This technique allow the attacker to generate domain address without raising any suspicion. The attacker controls which address DOKI will contact by transferring a specific amount of Dogecoin from his or her wallet. The attacker has complete control as only he have the access when and how much dogecoin to transfer, switching the domain accordingly. It, then, detects whether the value returned after query to API is zero. In that case, it will exit before continuing.
If the value returned by API is not zero, then it will download a shell script by contacting its C2 via HTTPS, using the URL
DOKI will then read from STDIN, waiting for binary data from that shell script. If data is received via STDIN, it saves itself as a file under /tmp, choosing its name randomly from a predefined list of Linux kernel modules
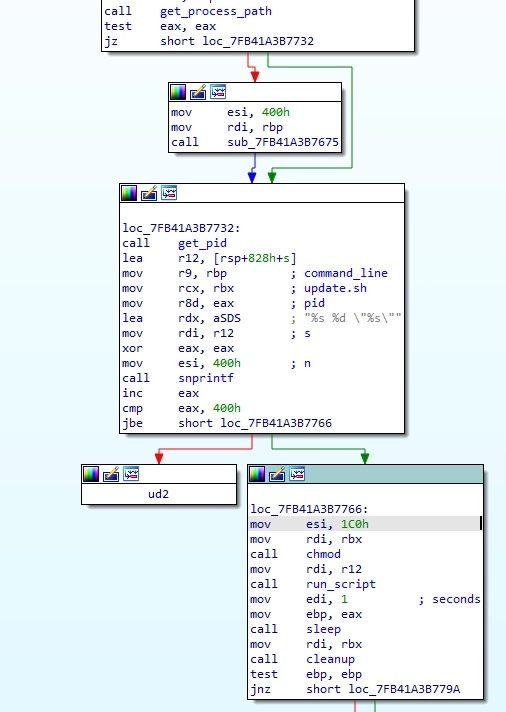
In the end, malware will fork to create child process which then executes the file and main function will return to repeat its logic flow.
Indicators of compromise:
Files:
- 4aadb47706f0fe1734ee514e79c93eed65e1a0a9f61b63f3e7b6367bd9a3e63b
- 6d77335c4f23[d0t]ddns[d0t]net
Countermeasures and Best practices for prevention:
- Companies and individuals owning container servers in the cloud must immediately fix configuration to prevent exposure which include checking for any exposed ports, verifying there are no foreign or unknown containers among the existing containers, and monitoring excessive use of resources.
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only.
- Do not download or open attachment in emails received from untrusted sources or unexpectedly received from trusted users.
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
- Confirm that the banking/financial app you’re using is the official, verified version.
References:


