Adrozek Malware
Original Issue Date:- December 11, 2020
Virus Type:- Browser modifiers
Severity:- Medium
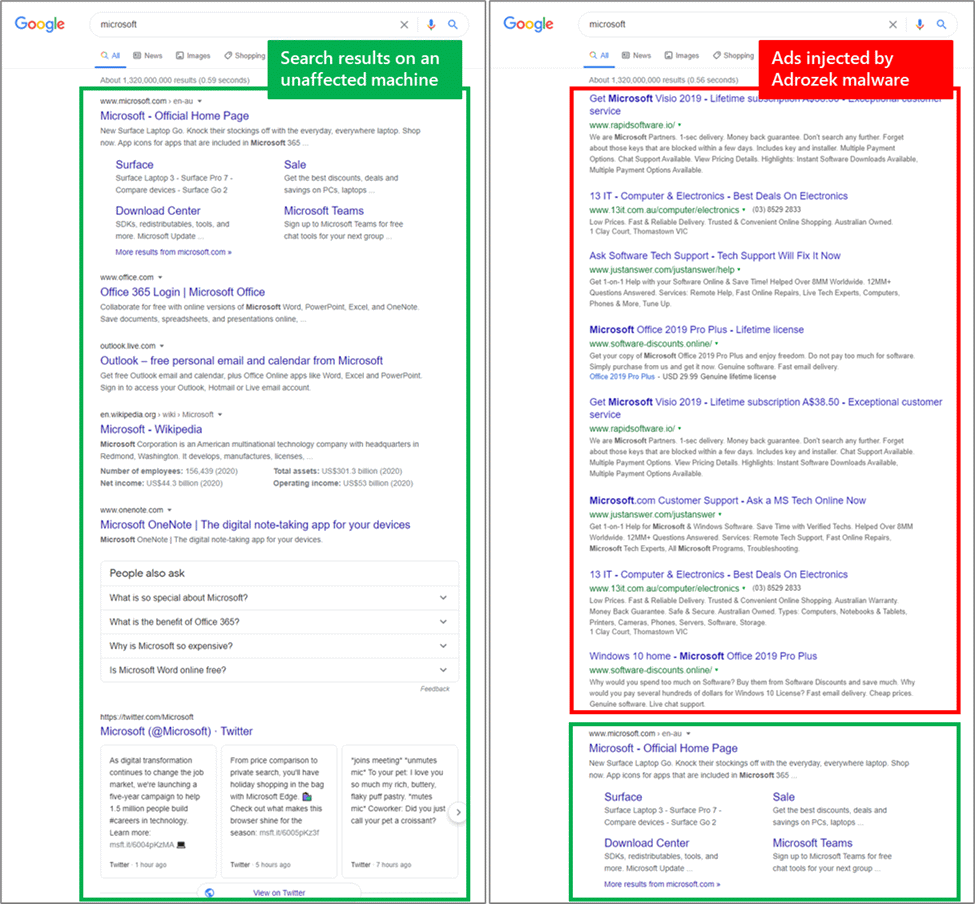
It has been reported that a new malware named Adrozek is affecting user’s device globally. It infects the device and then proceeds to modify web browsers and their settings in order to inject ads into search results pages.
Infection Mechanism:
The malware is distributed via classic drive-by download schemes. Users are typically redirected from legitimate sites to shady domains where they are tricked into installing malicious software. The software installs the Adrozek malware, which then proceeds to obtain reboot persistence with the help of a registry key. The malware looks for locally installed browsers such as Microsoft Edge, Google Chrome, Mozilla Firefox, Yandex Browser and attempts to force-install an extension by modifying the browser's AppData folders. It also modifies some of the browsers' DLL files to change browser settings and disable security features to make sure that browser’s security features doesn’t detect unauthorized modifications, modifications performed by Adrozek include:
- Disabling browser updates.
- Disabling file integrity checks.
- Disabling the Safe Browsing feature.
- Registering and activating the extension they added in a previous step.
- Allowing their malicious extension to run in incognito mode.
- Allowing the extension to run without obtaining the appropriate permissions.
- Hiding the extension from the toolbar.
- Modifying the browser's default home page.
- Modifying the browser's default search engine.
Adrozek’s attack chain is shown as under:
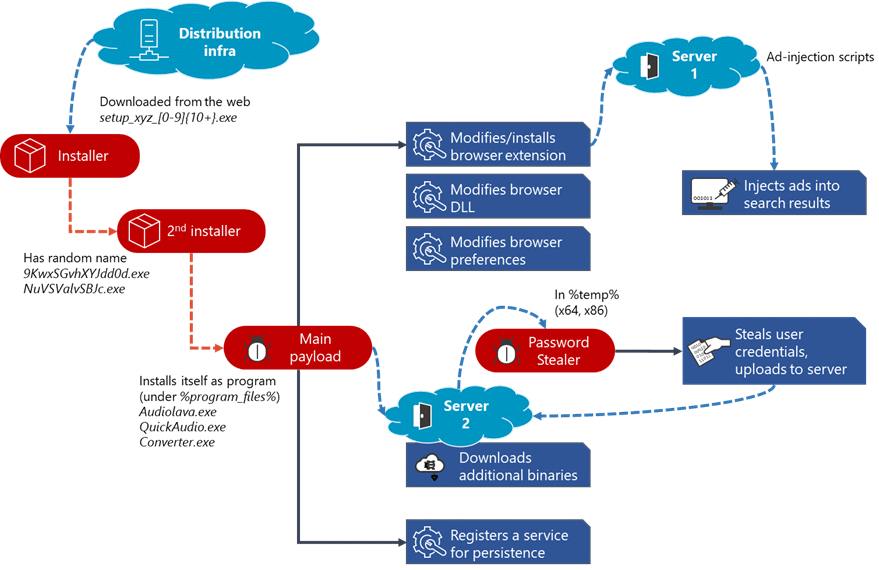
The attackers earn through affiliate advertising programs, which pay by amount of traffic referred to the sponsored affiliated pages.
Modified relevant DLL on targeted browsers:
| Browser | Extension paths examples |
|---|---|
| Microsoft Edge | %localappdata%\Microsoft \Edge\User Data\Default \Extensions \fcppdfelojakeahklfgkjegnpbgndoch |
| Google Chrome | %localappdata% \Google\Chrome \User Data\Default\Extensions \pkedcjkdefgpdelpbcmbmeomcjbeemfm (might vary) |
| Mozilla Firefox | %appdata%\Roaming \Mozilla\Firefox\Profiles \[profile]\Extensions \{14553439-2741-4e9d-b474-784f336f58c9} |
| Yandex Browser | %localappdata% \Yandex\YandexBrowser \User Data\Default\Extensions \fcppdfelojakeahklfgkjegnpbgndoch |
Countermeasures and Best practices for prevention:
Users and administrators are advised to take the following preventive measures to protect their devices:
- Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
- Users are advised to update their devices with patches as & when released by respective OEM.
- If devices found infected, it is recommended to re-install the browsers.
- Be aware of the risks of downloading and installing software from untrusted sources and clicking ads or links on suspicious websites.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser
- Users are advised to enable URL filtering solutions on browsers to prevent such attacks.
- Users are advised to use Antivirus solutions which uses behaviour-based, machine learning-powered detections to block Adrozek.
- Users are advised to use “Browser JSGuard” to detect and defend malicious HTML & JavaScript attacks through web browser based on Heuristics.
Download Link:- For Firefox Web Browser:
https://addons.mozilla.org/en-US/firefox/addon/browser-jsguard/ - For Google Chrome Web Browser:
https://chrome.google.com/webstore/detail/browserjsguard/ncpkigeklafkopcelcegambndlhkcbhb
References:
- https://www.microsoft.com/security/blog/2020/12/10/widespread-malware-campaign-seeks-to-silently-inject-ads-into-search-results-affects-multiple-browsers/
- https://www.zdnet.com/article/microsoft-exposes-adrozek-malware-that-hijacks-chrome-edge-and-firefox/
- Cyber Swachhta Kendra - Security Tools Section


